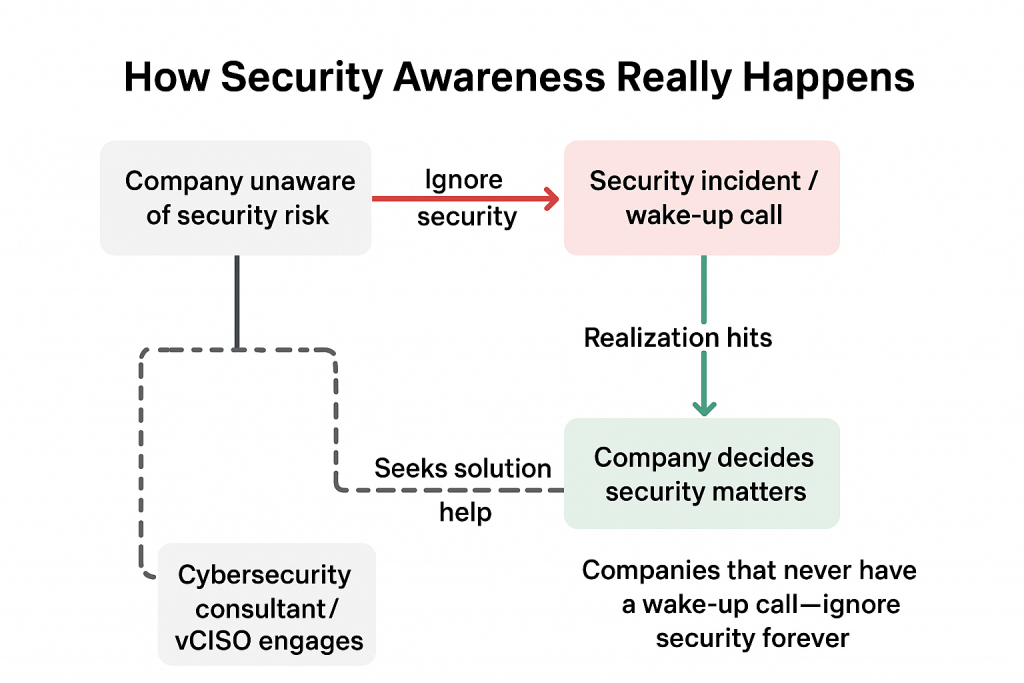
🔥 Truth bomb from a experience: You can’t make companies care about security.
Most don’t—until they get burned.
Security isn’t important… until it suddenly is. And by then, it’s often too late. Just ask the businesses that disappeared after a cyberattack.
Trying to convince someone it matters? Like telling your friend to eat healthy—they won’t care until a personal wake-up call hits.
Here’s the smarter play: focus on the people who already value security. Show them why you’re the one who can solve their problems. That’s where your time actually pays off.
Your energy shouldn’t go into preaching; it should go into actionable impact for those ready to act.
⏳ Remember: people only take security seriously when they decide it’s worth it. Your job is to be ready when that moment comes.
Opinion:
This perspective is spot-on. Security adoption isn’t about persuasion; it’s about timing and alignment. The most effective consultants succeed not by preaching to the uninterested, but by identifying those who already recognize risk and helping them act decisively.
#CyberSecurity #vCISO #RiskManagement #AI #CyberResilience #SecurityStrategy #Leadership #Infosec
ISO 27001 assessment → Gap analysis → Prioritized remediation → See your risks immediately with a clear path from gaps to remediation.

Start your assessment today — simply click the image on above to complete your payment and get instant access – Evaluate your organization’s compliance with mandatory ISMS clauses through our 5-Level Maturity Model — until the end of this month.
Let’s review your assessment results— Contact us for actionable instructions for resolving each gap.
InfoSec Policy Assistance – Chatbot for a specific use case (policy Q&A, phishing training, etc.)
Click above to open it in any web browser
Why Cybersecurity Fails in America
- From Prediction to Autonomy: Mapping AI Risk to ISO 42001, NIST AI RMF, and the EU AI Act
- The Hidden Battle: Defending AI/ML APIs from Prompt Injection and Data Poisoning
- Burp Pro Can Help With with Smart Contract
- 10 Global Risks Every ISO 27001 Risk Register Should Cover
- Why a Cyberattack Didn’t Kill iRobot—But Exposed Why It Failed
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory | ISO 27k Chat bot | Comprehensive vCISO Services | ISMS Services | Security Risk Assessment Services | Mergers and Acquisition Security




