Because of financial incentive, malicious software threats are real and attackers are using the web to gain access to corporate data. Targeted malicious software’s are utilized to steal intellectual property and other confidential data, which is sold in the black market for financial gain. With use of social media in corporate arena, organizations need to have web services use policy, to ensure employees use the internet for business and comply with company web use policies. To have an effective web use policy makes business sense and to implement this policy efficiently is not only due diligence but also assist in compliance. After implementing, the key to the success of web use policy is to monitor the effectiveness of the policy on regular basis.
Hosted web security services operate at the internet level, intercepting viruses, spyware and other threats before they get anywhere near your network. These days if malicious software has infected your gateway node the attacker is home free and it is basically game over. How to fight this malice is to use hosted web security services, which is transparent to users and stop the malwares before they get to the corporate network.
Things to look at web security hosted services are protection, control, security, recovery and multilayer protection.
Protect your corporation from anti-virus, anti-spam, and anti-spyware
Content Control of images, URL filtering and enterprise instant messages, all web request are checked against the policy
Secure email with encryption
Archive email for recovery
Multilayer protection against known and unknown threats including mobile user protection
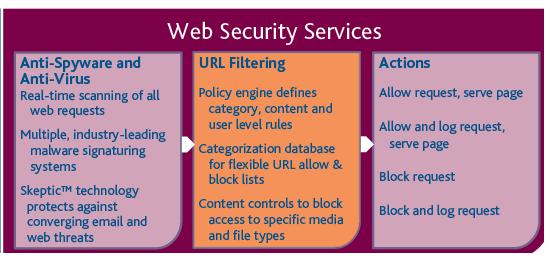
Web Security Anti-Virus, Anti-Spyware – stops web-borne spyware and viruses before they infiltrate your network, protecting your business from information theft and costly diminished network performance.
Web Filtering – enables you to block access to unwanted websites by URL, allowing you to control Internet use and enforce acceptable Internet usage policies
Download a free guide for the following hosted solutions
Hosted email solution
Hosted email archiving
Hosted web monitoring
Hosted online backup



