To become a successful business in today’s market, optimized information security controls may be the panacea for unmet security needs. One way to achieve optimized information security control is to perform ISO assessment and assess the organization security posture based on ISO 27002 code of practice and map each control with Capability Maturity Model Integration (CMMI) to find out the current CMMI level for each control.  The goal is to address the organization security needs as a whole, and assess how different departments and business functions are addressing the current business security requirements. The CMMI has five levels and evaluate security controls based on levels, not on specific objectives. Each level provides the basis for the next level where it is not possible to get to the next level without complying with previous level. ISO 27002 is a comprehensive framework which can be utilized to obtain the baseline upon which to build each level. For each control in ISO 27002, maturity levels are defined using maturity definition found in CMMI. In the assessment report maturity level of each control of ISO 27002 standard can be evaluated. Utilizing the color coded scheme provided by CMMI model, create a one page ISO control summary for executives which will not only help them to understand the current security posture but also can be instrumental for measuring progress and resource allocation.
The goal is to address the organization security needs as a whole, and assess how different departments and business functions are addressing the current business security requirements. The CMMI has five levels and evaluate security controls based on levels, not on specific objectives. Each level provides the basis for the next level where it is not possible to get to the next level without complying with previous level. ISO 27002 is a comprehensive framework which can be utilized to obtain the baseline upon which to build each level. For each control in ISO 27002, maturity levels are defined using maturity definition found in CMMI. In the assessment report maturity level of each control of ISO 27002 standard can be evaluated. Utilizing the color coded scheme provided by CMMI model, create a one page ISO control summary for executives which will not only help them to understand the current security posture but also can be instrumental for measuring progress and resource allocation.
The scope of the ISO27k standards includes various aspects of IT. The introduction to ISO 27002 states clearly: “Information can exist in many forms. It can be printed or written on paper, stored electronically, transmitted by post of using electronic means, shown on films, or spoken in conversation. Whatever form information takes, or means by which it is shared or stored, it should always be appropriately protected.”
Benefits of ISO 27k framework:
o Framework addresses the security issues for the whole organization and limit data breaches
o Address compliance with various regulations like (SOX, HIPAA, and PCI) without creating silos.
o Reduce total cost of security by decreasing total number of controls required
o Perception of your business that you are serious about information security not just compliance
o Enhance partners and vendors confidence to do business with your organization
o Future deciding factor for national and especially international partners for more business
o Internationally recognized standard which addresses security awareness for the whole organization

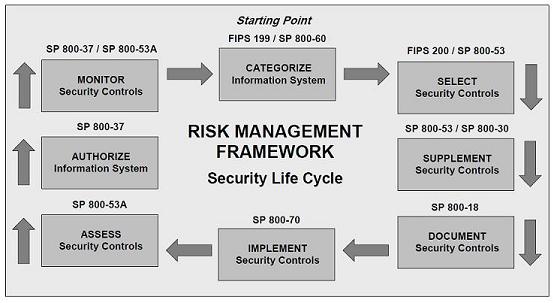
Assessment will give an organization a high level view of their current security posture and provide a road map for security strategy in a sense what needs to be addressed first utilizing risk based approach. This is also a good start if your organization is interested in the Information Security Management System (ISMS) or ISO 27001 certification. ISO 27001 is the standard for the certification which includes the set of requirements for ISMS. Justifiable scoping is the key to a quick and successful certification; organization may adjust their scope in a re-certification attempt. Perhaps in the first attempt you may need to include just a web portal in your scope and the entire infrastructure behind supporting that portal. Once the ISMS project scope is determined, here are some steps you can follow to prepare for ISO 27001 auditors.
1. Based on your scope, create an asset list
2. Find out asset threats and vulnerabilities and classify the asset based on CIA scale
3. Come up with risk matrix based on impact and likelihood of the risk
4. Create priorities based on impact and likelihood of the risk
5. Based on priorities, implement appropriate controls for risks which needs to be addressed
6. Do the risk assessment again, PDCA improve ISMS
“ISO27001 is a structured, technology-neutral, vendor-agnostic specification and code of practice for information security management in organizations of all sizes that should be adopted as part of an organization’s overall risk management strategy.”
This should give you a jump start to certification. You have already started the process of certification because most of the documentations in the risk assessment will become part of certification process later and will lead you to 12 steps which are part of PDCA cycle. ISMS certification process utilized Plan-Do-Check-Act (PDCA) cycle methodology which continually improve information security management system and meet the contractual, legal, and regulatory requirements for information security.
ISO assessment is utilized to analyze the current security posture of an organization where each control is defined and can be color coded using the base definition found in CMMI. Therefore ISO assessment is a great first step towards the final ISO 27001 certification audit or for that matter any compliance audit.
[TABLE=2]
ISO 27k framework for today’s security challenges
httpv://www.youtube.com/watch?v=yRFMfiLbNj8
Three useful titles on ISO 27k by Alan Calder
Tags: Capability Maturity Model Integration, CIA scale, Information Security, Information Security Management System, International Organization for Standardization, isms, iso 27001, iso 27002, ISO/IEC 27001, PCI, PDCA, Risk Assessment, Risk management, Security, SOX HIPAA, vsrisk


![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=29e8a09f-ad38-4356-a22d-9b190f1eb225)

![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=75ca6076-5285-4eaa-9251-01afd6576cbb)
 The goal is to address the organization security needs as a whole, and assess how different departments and business functions are addressing the current business security requirements. The CMMI has five levels and evaluate security controls based on levels, not on specific objectives. Each level provides the basis for the next level where it is not possible to get to the next level without complying with previous level.
The goal is to address the organization security needs as a whole, and assess how different departments and business functions are addressing the current business security requirements. The CMMI has five levels and evaluate security controls based on levels, not on specific objectives. Each level provides the basis for the next level where it is not possible to get to the next level without complying with previous level. 



