ISO 27001 is an internationally recognized Information Security Standard that is widely acclaimed. It is published by the International Organization for Standardization (ISO) and provides a certifiable framework comprising security policies and procedures. The standard aims to assist organizations in safeguarding their data by implementing an Information Security Management System (ISMS).
To obtain ISO 27001 certification, organizations must fulfill the requirements for establishing, implementing, maintaining, and continuously improving an Information Security Management System (ISMS) that aligns with their specific business needs. The ISO 27001 standard consists of two distinct parts: Clauses and Annex A. The Clauses outline the general requirements for an ISMS, while Annex A provides a set of controls and objectives that organizations can choose to implement based on their risk assessment and security requirements.
Clauses 4-10 in ISO 27001 consist of mandatory requirements that all organizations seeking certification must fulfill. Each clause includes several sub-requirements. Here is a brief overview of each clause:
- Clause 4: Context of the Organization – Organizations must determine the scope of their ISMS, identify internal and external issues relevant to information security, and define the interested parties.
- Clause 5: Leadership – Top management should demonstrate leadership and commitment to the ISMS by establishing policies, assigning responsibilities, and promoting awareness.
- Clause 6: Planning – This clause emphasizes the importance of risk assessment and treatment, setting objectives, and planning to achieve them.
- Clause 7: Support – Organizations must provide the necessary resources, competence, awareness, communication, and documented information to support the ISMS.
- Clause 8: Operation – This clause covers the implementation of risk treatment plans, management of changes, and effective operation of controls and processes.
- Clause 9: Performance Evaluation – Organizations need to monitor, measure, analyze, and evaluate the performance of the ISMS and conduct internal audits.
- Clause 10: Improvement – This clause focuses on nonconformities, corrective actions, continual improvement, and the management of incidents and improvements.
Meeting these mandatory requirements is crucial for organizations seeking ISO 27001 certification.
Annex A of ISO 27001 comprises a collection of security controls that are not obligatory but can be selectively implemented based on the specific needs of an organization. By conducting a risk assessment, organizations can identify the security controls that align with their security program and effectively address their risks and vulnerabilities. This approach allows organizations to tailor the implementation of controls to their unique requirements and enhance their overall information security posture.
After establishing the necessary policies, procedures, and documentation for ISO 27001 compliance and ISMS is operational, organizations can engage an accredited certification body to perform an audit. This audit assesses the implementation and effectiveness of the Information Security Management System (ISMS) against the ISO 27001 requirements. If the audit is successful and the organization meets all the necessary criteria, an ISO 27001 certificate will be issued, validating the organization’s adherence to the standard and their commitment to information security.
By adhering to ISO 27001 standards, organizations can establish robust policies, procedures, and technology measures that effectively safeguard their data, regardless of its location. This comprehensive approach significantly reduces the risk of cyber-attacks and fosters a culture of information security within the organization.
Obtaining ISO 27001 certification serves as a notable competitive advantage for businesses, irrespective of their industry or size. The certification acts as concrete evidence to customers that the organization is dedicated to protecting their data and fulfilling contractual security obligations. Moreover, ISO 27001 certification holds international recognition, making it instrumental in expanding global business opportunities and establishing trust with partners worldwide.
DISC LLC offers the expertise of a team comprised of former ISO auditors and experienced practitioners who can assist in preparing your organization for a successful ISO 27001 audit. Their services aim to guide you towards certification by identifying and addressing any gaps that may exist within your current security program. They provide support in implementing the required policies, procedures, and technologies to meet the ISO 27001 standards. With their knowledge and experience, DISC LLC can help your organization navigate the certification process and ensure a solid foundation for information security.
Following the attainment of ISO 27001 certification, we offer services to manage and maintain your Information Security Management System (ISMS). Our expert team will diligently oversee and guide your ISMS to ensure ongoing compliance with ISO 27001 requirements, thereby facilitating future certifications. By entrusting us with the management of your ISMS, you can focus on your core business activities while maintaining the necessary level of information security and sustaining your commitment to ISO 27001 standards.
We’d love to hear from you! If you have any questions, comments, or feedback, please don’t hesitate to contact us. Our team is here to help and we’re always looking for ways to improve our services. You can reach us by email (info@deurainfosec.com), or through our website’s contact form.
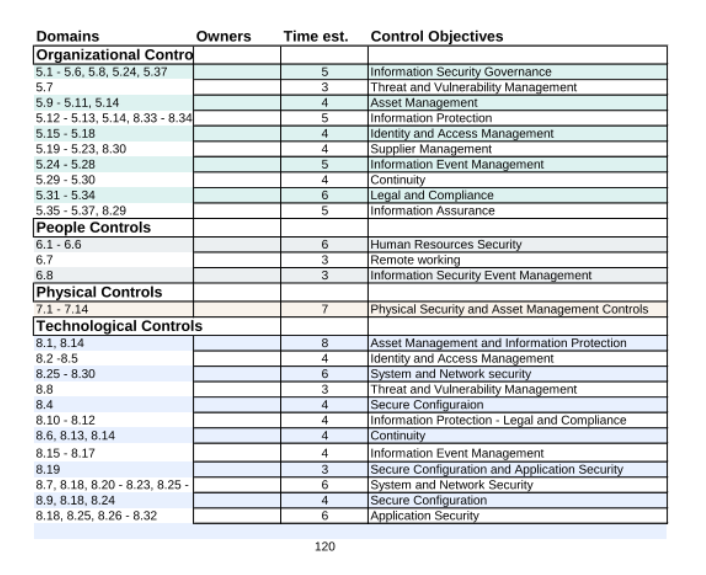
Transition plan from ISO 27001 2013 to ISO 27001 2022
Why the updated ISO 27001 standard matters to every business’ security
Detailed explanation of 11 new security controls in ISO 27001:2022
6 Pocket eBooks every ISO professional should read
Tool for defining the ISO 27001 ISMS scope
Risk Management document templates
ISO 27001 & ISO 27017 & ISO 27018 CLOUD DOCUMENTATION TOOLKIT
IMPLEMENT ISO 27001 AND ISO 22301 EFFORTLESSLY
How to Maintain ISO 27001 Certification: 7 Top Tips
Implementing an ISMS – The nine Steps approach
ISO 27001 CyberSecurity Toolkit
Enhance your privacy management with ISO 27701
ISO/IEC 27701 2019 Standard and Toolkit
InfoSec tools | InfoSec services | InfoSec books