Eliminating SQL Injection Vulnerabilities in Software

SQL Injection Strategies: Practical techniques to secure old vulnerabilities against modern attacks
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Mar 26 2024
Eliminating SQL Injection Vulnerabilities in Software

SQL Injection Strategies: Practical techniques to secure old vulnerabilities against modern attacks
InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Sep 21 2023
MOVEit transfer service pack has been discovered with three vulnerabilities associated with SQL injections (2) and a Reflected Cross-Site Scripted (XSS). The severity for these vulnerabilities ranges between 6.1 (Medium) and 8.8 (High).
Progress-owned MOVEit transfer was popularly exploited by threat actors who attacked several organizations as part of a ransomware campaign. The organizations previously reported to be affected by MOVEit vulnerability include Shell, BBC, British Airways, CalPERS, Honeywell, and US government agencies.
This SQL injection vulnerability was discovered on the MOVEit Transfer machine interface, which could lead to gaining unauthorized access to the MOVEit Transfer database. A threat actor could exploit this vulnerability by submitting a crafted payload to the MOVEit Transfer machine interface.
Successful exploitation could result in the modification and disclosure of MOVEit database content. However, a threat actor must be authenticated to exploit this vulnerability. Progress has given the severity of this vulnerability as 8.8 (High).
Products affected by this vulnerability include MOVEit Transfer, either MySQL or MSSQL DB, all versions. Users are recommended to upgrade to the September Service Pack to fix this vulnerability.
This other SQL injection vulnerability exists in the MOVEit Transfer web interface, which could possibly lead to gaining unauthorized access to the MOVEit Transfer database. A threat actor could exploit this vulnerability by submitting a crafted payload to the MOVEit Transfer web interface.
Successful exploitation could result in the modification and disclosure of MOVEit database content. The prerequisite for a threat actor to exploit this vulnerability includes access to a MOVEit system administrator account. Progress has given the severity of this vulnerability as 7.2 (High).
Products that are affected by this vulnerability include MOVEit Transfer, either MySQL or MSSQL DB, all versions. To prevent this vulnerability, users are recommended to Upgrade to the September Service Pack and limit sysadmin account access.
This Reflected XSS vulnerability was found in the MOVEit Transfer’s web interface, which a malicious payload can exploit during the package composition procedure. A threat could craft a malicious payload and target MOVEit Transfer users. When interacting with the payload, the threat actor can execute malicious JavaScript on the victim’s browser.
Progress has given the severity of this vulnerability as 6.1 (Medium). Products affected due to this vulnerability include MOVEit Transfer, either MySQL or MSSQL DB, all versions. To prevent this vulnerability, users are recommended to Upgrade to September Service Pack and limit sysadmin account access.
A comprehensive list of vulnerable product versions, documentation, release notes, and fixed versions has been given below.
| Affected Version | Fixed Version (Full Installer) | Documentation | Release Notes |
| MOVEit Transfer 2023.0.x (15.0.x) | MOVEit Transfer 2023.0.6 (15.0.6) | MOVEit 2023 Upgrade Documentation | MOVEit Transfer 2023.0.6 Release Notes |
| MOVEit Transfer 2022.1.x (14.1.x) | MOVEit Transfer 2022.1.9 (14.1.9) | MOVEit 2022 Upgrade Documentation | MOVEit Transfer 2022.1.9 Release Notes |
| MOVEit Transfer 2022.0.x (14.0.x) | MOVEit Transfer 2022.0.8 (14.0.8) | MOVEit 2022 Upgrade Documentation | MOVEit Transfer 2022.0.8 Release Notes |
| MOVEit Transfer 2021.1.x (13.1.x) | MOVEit Transfer 2021.1.8 (13.1.8) | MOVEit 2021 Upgrade Documentation | MOVEit Transfer 2021.1.8 Release Notes |
| MOVEit Transfer 2021.0.x (13.0.x) or older | Must Upgrade to a Supported Version | See MOVEit Transfer Upgrade and | N/A |
| Migration Guide |
A security advisory has been released by Progress which includes a comprehensive list of the affected products and the vulnerabilities that have been identified.

InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Sep 18 2023
TransUnion is an American consumer credit reporting agency. TransUnion collects and aggregates information on over one billion individual consumers in over thirty countries, including “200 million files profiling nearly every credit-active consumer in the United States”.
A threat actor who goes by the moniker “USDoD” announced the leak of highly sensitive data allegedly stolen from the credit reporting agency. The leaked database, over 3GB in size, contains sensitive PII of about 58,505 people, all across the globe, including the America and Europe
According to researchers vx-underground who reported the leak, the archive contains data that dates back to March 2nd, 2022, which could be the data of the data breach.
This leaked database has information on individuals all across the globe including the Americas (North and South), as well as Europe
vx-underground states that leaked data includes individual first name, last name, Internal TransUnion identifiers, sex, passport information, place of birth, date of birth, civil status, age, current employer, information on their employer, a summary of financial transactions, credit score, loans in their name, remaining balances on the loans, where they got the loan from, when TransUnion first began monitoring their information.
The name USDoD is well known in the cyber security sector, it was also listed in the indictment for the notorious owner of the BreachForums cybercrime forum Pompompurin. vx-underground pointed out that they are believed to be behind many other high-profile security breaches.
Recently, The multinational aerospace corporation Airbus announced that it is investigating a data leak after cybersecurity firm Hudson Rock reported that a hacker posted information on thousands of the company’s vendors to the dark web.
“USDoD” announced he had gained access to an Airbus web portal by compromising the account of a Turkish airline employee.
The hacker claimed to have details on thousands of Airbus vendors. The threat actors obtained the personal information of 3,200 individuals associated with Airbus vendors, exposed data include names, job titles, addresses, email addresses, and phone numbers.
In December 2022, the FBI’s InfraGard US Critical Infrastructure Intelligence portal was hacked and a database containing the contact details of more than 80,000 high-profile private sector individuals was offered for sale by USDoD on the Breached cybercrime forum.
After the law enforcement shutdown of “Breached” forum, its members, including “USDoD,” moved to other platforms such as “BreachForums.”
“USDoD” posted two threads on this new forum, one to announce they have joined the notorious ransomware group Ransomed. In the second threat, the hacker exposed the personal information of 3,200 sensitive Airbus vendors. USDoD also warned that Lockheed Martin and Raytheon might be the next targets.
“Threat actors typically refrain from revealing their intrusion techniques, however in this exceptionally rare leak, “USDoD” revealed they gained access to Airbus’s data by exploiting “employee access from a Turkish Airline”.” reported Hudson Rock. “Using this information, Hudson Rock researchers succeeded to trace the mentioned employee access — a Turkish computer infected with an info-stealing malware in August 2023.”
According to the researchers, the computer of the victim was likely infected with the RedLine stealer after he attempted to download a pirated version of the Microsoft .NET framework.

A Business Guide for Protecting Sensitive Information
InfoSec tools | InfoSec services | InfoSec books | Follow our blog | DISC llc is listed on The vCISO Directory
Aug 15 2023
e. It has an impressive history that spans over 30 years, and now it serves as an effective object-relational database system that is open source. Because of its ability to store and grow even the most complex data workloads, it has become the database of choice for a wide variety of applications, ranging from websites to mobile and analytics systems.It has been discovered that the widely used open-source object-relational database system PostgreSQL has a significant security flaw. The vulnerability, identified as CVE-2023-39417, has a significant CVSS score of 7.5 and gives an attacker the ability to execute arbitrary code as the bootstrap superuser if the attacker also has the capability to create databases at the database level.The vulnerability may be exploited in the PostgreSQL extension script if an administrator has installed files of a vulnerable, trusted, non-bundled extension. The vulnerability is present in the PostgreSQL extension script. When using the @extowner@, @extschema@, or @extschema:…@ functions, there is a security flaw because user input is not properly sanitized. This flaw is the root source of the vulnerability.
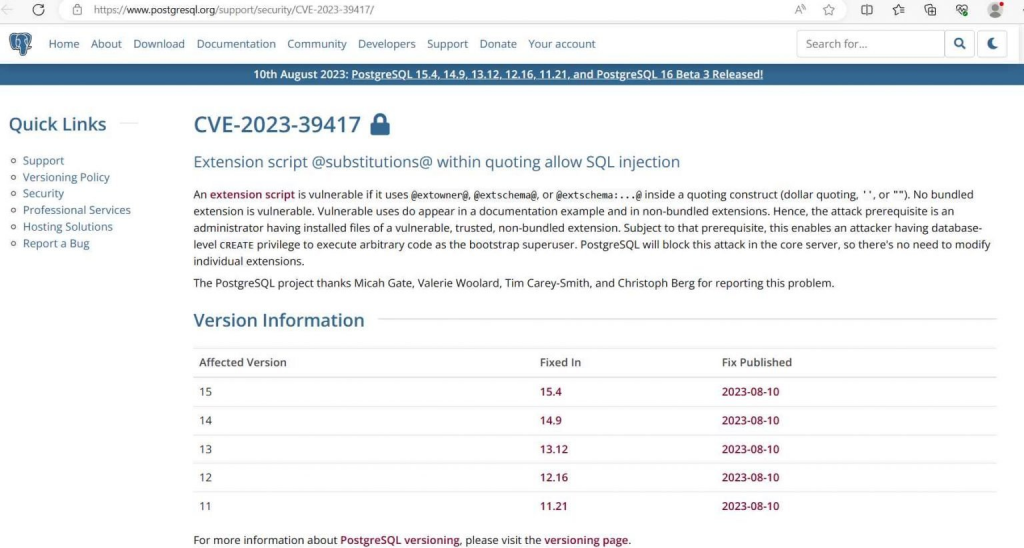
An adversary may take advantage of this flaw by sending malicious data to a PostgreSQL database that is running a version of the program that is susceptible to being exploited. It’s possible that the malicious input will be in the form of a SQL query, or it may be a parameter to a function. As soon as the attacker submits the malicious input, they are able to execute arbitrary code in the context of the bootstrap superuser.
The bootstrap superuser is a unique user account that has full authority over a PostgreSQL database. This account is only accessible via the bootstrap script. This indicates that an adversary who is able to run arbitrary code as the bootstrap superuser has the ability to do whatever they want with the database. This includes stealing data, deleting data, or altering data.
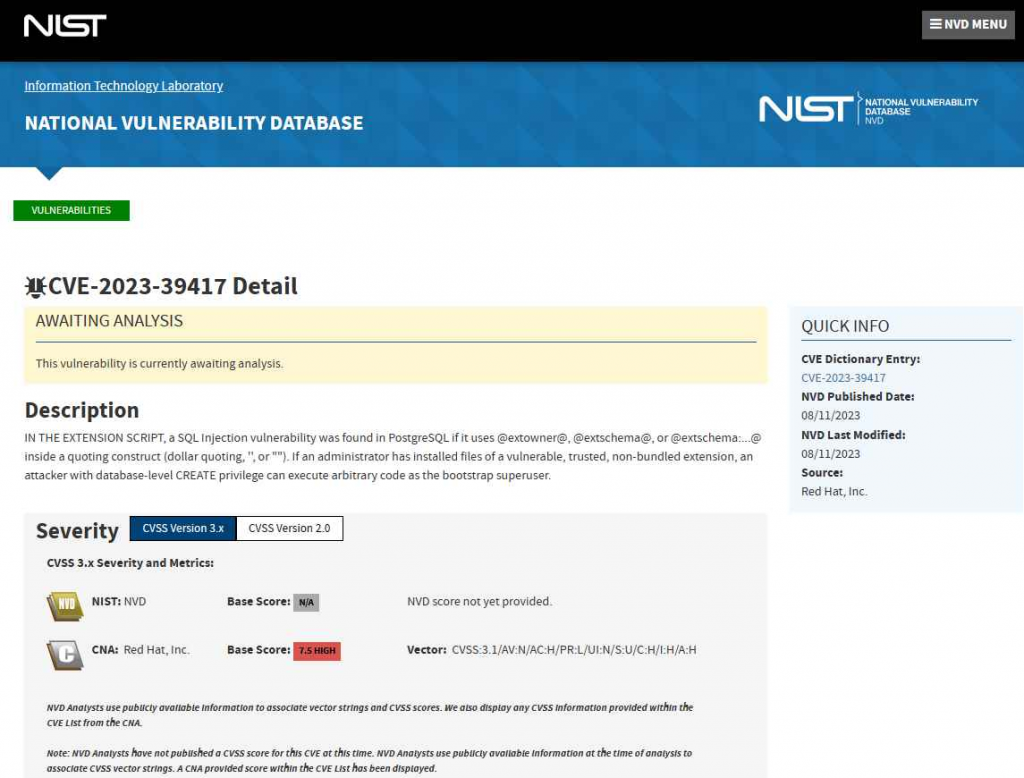
All of the PostgreSQL versions 11, 12, 13, 14, and 15 are susceptible to the CVE-2023-39417 issue. The fixed versions are 11.21, 12.16, 13.12, 14.9, and 15.4. PostgreSQL has made available a patch that prevents this attack from taking place at the fundamental level of the server. The process of remediation is made more straightforward by the fact that users do not have to edit individual extensions. It is imperative that you install this necessary update as soon as possible since the safety of your data relies on it.
SQL Injection Strategies: Practical techniques to secure old vulnerabilities against modern attacks
InfoSec tools | InfoSec services | InfoSec books
Jul 17 2023
In this Help Net Security interview, Charles Brooks, Adjunct Professor at Georgetown University’s Applied Intelligence Program and graduate Cybersecurity Programs, talks about how zero trust principles, identity access management, and managed security services are crucial for effective cybersecurity, and how implementation of new technologies like AI, machine learning, and tracking tools can enhance supply chain security.
The loss of data despite protection measures is not that surprising. We are all playing catchup in cybersecurity. The internet was invented in a government laboratory and later commercialized in the private sector. The hardware, software, and networks were originally designed for open communication. Cybersecurity initially was not a major consideration. That mindset has surely changed due to the explosion of connectivity and commerce on the internet and CISOs are playing a big game of catch up too.
There are a multitude of causes that can account for the exfiltration of sensitive data. The first being that hacker adversaries have become more sophisticated and capable of breaching. The basic tools and tactics hackers use for exploitation include malware, social engineering, phishing (the easiest most common, especially spear-phishing aimed at corporate executives), ransomware, insider threats, and DDOS attacks. Also, they often use advanced and automated hacking tools shared on the dark web, including AI and ML tools that are used to attack and explore victims’ networks. That evolving chest of hacker weaponry is not so easy for CISOs to defend against.
Another big factor is the reality is that exponential digital connectivity propelled by the COVID-19 pandemic has changed the security paradigm. Many employees now work from hybrid and remote offices. There is more attack surface area to protect with less visibility and controls in place for the CISO. Therefore, it is logical to conclude that more sensitive data has and will be exposed to hackers.
The notion of adequate protection is a misnomer as threats are constantly morphing. All it takes is one crafty phish, a misconfiguration, or a failure to do a timely patch for a gap to provide an opportunity for a breach. Finally, many CISOs have had to operate with limited budgets and qualified cyber personnel. Perhaps they have lower expectations of the level of security they can achieve under the circumstances.
CISOs must enact a prudent risk management strategy according to their industry and size that they can follow to allow them to best optimize resources. A good risk management strategy will devise a vulnerability framework that Identifies digital assets and data to be protected. A risk assessment can quickly identify and prioritize cyber vulnerabilities so that you can immediately deploy solutions to protect critical assets from malicious cyber actors while immediately improving overall operational cybersecurity. This includes protecting and backing up business enterprise systems such as: financial systems, email exchange servers, HR, and procurement systems with new security tools (encryption, threat intel & detection, firewalls, etc.) and policies.
There are measures in a vulnerability framework that are not cost prohibitive. Those measures can include mandating strong passwords for employees and requiring multi-factor authentication. Firewalls can be set up and CISOs can make plans to segment their most sensitive data. Encryption software can also be affordable. The use of the cloud and hybrid clouds enables implementation of dynamic policies, faster encryption, drives down costs, and provides more transparency for access control (reducing insider threats). A good cloud provider can provide some of those security controls for a reasonable cost. Clouds are not inherently risky, but CISOs and companies will need to recognize that they must thoroughly evaluate provider policies and capabilities to protect their vital data.
And if a CISO is responsible for protecting a small or medium business without a deep IT and cybersecurity team below them, and are wary of cloud costs and management, they can also consider outside managed security services.
This goes to the essence of the strategy of zero trust. Zero trust (ZT) is the term for an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources. Organizations need to know everything that is connected to the network, devices & people.
Identity access management or IAM, is very important. IAM the label used for the set of technologies and policies that control who accesses what resources inside a system. A CISO must determine and know who has access to what data and why. If an employee leaves, they need to immediately revoke privileges and ensure that nothing sensitive was removed from the organization. There are many good IAM tools available from vendors on the market.
Certainly, with employee turnover, there are ethical and trust elements involved. Employee insider threats are difficult to detect and manage. Some of that can be addressed upfront in employment contracts with an employee understanding of the legal parameters involved, it is less likely that they will run off with sensitive data.
Yes, the burnout is a direct result of CISOs having too many responsibilities, too little budget, and too few workers to run operations and help mitigate growing cyber-threats. Now the personal liability factors exemplified by as the class action suit against Solar’s Wind’s CISO, and the suit against Uber’s CISO for obscuring ransomware payments, has heightened the risk. In an industry that is already lacking in required numbers of cybersecurity leaders and technicians, CISOs need to be given not only the tools, but the protections necessary for them to excel in their roles. If not, the burnout and liability issues will put more companies and organizations at greater risk.
Despite the trends of greater frequency, sophistication, lethality, and liabilities associated with incursions, industry management has been mostly unprepared and slow to act at becoming more cyber secure. A Gartner survey found that 88% of Boards of Directors (BoDs) view cybersecurity as a business risk, as opposed to a technology risk, according to a new survey, and that only 12% of BoDs have a dedicated board-level cybersecurity committee.
“It’s time for executives outside of IT to take responsibility for securing the enterprise,” said Paul Proctor, Chief of Research for Risk and Security. “The influx of ransomware and supply chain attacks seen throughout 2021, many of which targeted operation- and mission-critical environments, should be a wake-up call that security is a business issue, and not just another problem for IT to solve.”
CISOs not only need a seat at the table in the C-Suite, but they also need insurance protections comparable to other executive management that limits their personal liability. There is no panacea for perfect cybersecurity. Breaches can happen to any company or person in our precarious digital landscape. It is not fair or good business to have CISO go at it alone. In a similar context, cybersecurity should no longer be viewed as a cost item for businesses or organizations. It has become an ROI that can ensure continuity of operations and protect reputation. Investment in both the company and the CISO’s compensation and portfolio of required duties need to be a priority going forward.
As supply chain risk continues to be a recurring priority, how can CISOs better manage this aspect of their cybersecurity strategies, especially under constrained budgets?
Ensuring that the supply chain is not breached including the design, manufacturing, production, distribution, installation, operation, and maintenance elements is a challenge to all companies. Cyber-attackers will always look for the weakest point of entry and mitigating third-party risk is critical for cybersecurity. Supply chain cyber-attacks can be perpetrated from nation-state adversaries, espionage operators, criminals, or hacktivists.
CISOs require visibility of all vendors in the supply chain along with set policies and monitoring. NIST, a non-regulatory agency of the US Department of Commerce has a suggested framework for supply chain security that provides sound guidelines from both government and industry.
NIST recommends:
Other mitigation efforts can be done with the acquisition of new technologies that monitor, alert, and analyze activities in the supply chain. Artificial intelligence and machine learning tools can provide visibility and predictive analytics, and stenographic and watermark technologies can provide tracking of products and software.

Previous DISC InfoSec posts on CISO topic

InfoSec tools | InfoSec services | InfoSec books
Apr 13 2023
Hackers were able to acquire access to individuals’ personal information after Hyundai announced a data breach that affected vehicle owners in Italy and France as well as those who had scheduled test drives with the automaker. According to Troy Hunt, the author of the website “HaveIBeenPwned,” the event has caused the personal data of clients to become public.
The letter also makes it clear that the individual who hacked into Hyundai’s database did not take any financial information or identifying numbers. It is unknown how many Hyundai customers have been impacted by this event, how long the network attack lasted, or what additional nations may be at risk. Customers of a South Korean automobile manufacturer are being cautioned to be wary of unsolicited e-mails and SMS messages that pretend to come from the company. These communications might be efforts at phishing or social engineering. In response to the incident, Hyundai claims it has enlisted the help of information technology specialists, who have taken the affected systems down while new security measures are put into place. In February of 2023, the business released emergency software patches for a number of car models that had been compromised by a simple hack with a USB cable, which had made it possible for criminals to take the vehicles.
On the other hand, the Japanese automaker Toyota has admitted that there may have been a breach of consumer data due to security flaws at its operations in Italy. Throughout the course of more than one and a half years, up until this past March, Toyota Italy carelessly disclosed confidential information. In particular, it divulged confidential information on its Salesforce Marketing Cloud and Mapbox APIs. Threat actors might utilize this information to their advantage to acquire access to the telephone numbers and email addresses of Toyota customers and then use those details to start phishing attacks on those customers. According to the findings of the research team at Cybernews, the organization exposed credentials to the Salesforce Marketing Cloud, which is a supplier of software and services related to digital marketing automation and analytics. Threat actors might get access to phone numbers and email addresses, as well as customer monitoring information, as well as the contents of email, SMS, and push-notification messages by abusing the data. Moreover, Toyota Italy exposed the application programming interface (API) tokens for the software business Mapbox. These tokens were used to access map data. Although while the data is not as sensitive as the credentials for the Salesforce Marketing Cloud, it is still possible for threat actors to misuse it in order to query a large number of queries and drive up Toyota’s API use costs.
Toyota is not the only automaker that has lately put itself as well as its consumers in Italy in a vulnerable position. In January of this year, the Indian branch of Toyota Motor announced a data breach, claiming that it was possible that the personal information of some of its customers had been exposed.

InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services

Apr 11 2023
Better to have USB data protection and not need it, than need it and not be prepared.

There are three things that I make sure I do when I’m out and about. I seek out the best coffee I can find. I make sure I use a VPN when using public Wi-Fi, and I always make sure I use a USB data blocker, otherwise known as a USB condom, whenever I use a third-party charger (such as those you find in coffee shops).
OK, first off, what on earth is a USB condom?
Also: FBI warns of public ‘juice jacking’ charging stations that steal your data. How to stay protected
A USB condom is a small dongle that adds a layer of protection between your device and the charging point you’re attaching it to.
Remember, USB isn’t just a charging protocol, it also allows data to flow back and forth, and while most of the time this data flow is safe, it is possible to create a malicious charging port that can do bad things, such as plant malware on your device or steal your data.
Buy the PortaPow USB | Data Blocker at Amazon
Source:
https://www.zdnet.com/article/protect-your-data-with-a-usb-condom/
Shockproof Carrying Case Hard Protective EVA Case Impact Resistant Travel 12000mAh Bank Pouch Bag USB Cable Organizer Earbuds Pocket Accessory Smooth Coating Zipper Wallet Rose Gold

InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services

Mar 13 2023
Businesses from all industries are aware of the benefits of cloud computing. Some organizations are just getting started with migration as part of digital transformation initiatives, while others are implementing sophisticated multi-cloud, hybrid strategies. However, data security in cloud computing is one of the most challenging deployment concerns at any level due to the unique risks that come with the technology.
The cloud compromises the conventional network perimeter that guided cybersecurity efforts in the past. As a result, a distinct strategy is needed for data security in cloud computing, one that takes into account both the complexity of the data compliance, governance, and security structures as well as the dangers.
The top investment businesses implementing digital transformation initiatives want to make over the next three years is bolstering cybersecurity defenses. A paradigm shift in cybersecurity is being brought about by the rising trend of remote and hybrid workplaces, which is altering investment priorities.
Cloud computing provides the underlying technology for this transition as organizations want to increase resilience, and people want the freedom to work from anywhere. Yet, the lack of built-in security safeguards in many cloud systems highlights the need for data security in cloud computing.

Cloud data security involves adopting technological solutions, policies, and processes to safeguard cloud-based systems and apps and the data and user access that go with them. The fundamental tenets of information security and data governance apply to the cloud as well:
Confidentiality: Protecting the data from illegal access and disclosure is known as confidentiality.
Integrity: Preventing unauthorized changes to the data so that it may be trusted
Accessibility: Making sure the data is completely accessible and available when it’s needed.
Cloud data security must be taken into account at every stage of cloud computing and the data lifecycle, including during the development, deployment, and administration of the cloud environment.
Cloud computing has revolutionized the way data is gathered, stored, and processed, but it has also introduced new risks to data security. As more organizations rely on the cloud, cyberattacks and data breaches have become the biggest threats to data protection. While cloud technology is subject to the same cybersecurity risks as on-premises solutions, it poses additional risks to data security.
Security flaws in APIs used for authentication and access are a common risk associated with the cloud. These flaws can be exploited by hackers to gain unauthorized access to sensitive data. Common issues include insufficient or improper input validation and insufficient authentication mechanisms. APIs can also be vulnerable to denial-of-service attacks (DoS), causing service disruptions and data loss.
Account takeover or hijacking is a common threat in cloud computing, where hackers gain unauthorized access to user accounts and can steal or manipulate sensitive data. Hackers can gain access to cloud accounts due to weak or stolen passwords used by users. This is because users often use simple, easy-to-guess passwords or reuse the same password across multiple accounts. Once a hacker gains access to one account, they can potentially access other accounts that use the same password.
Insider threats are a significant concern in cloud computing due to the lack of visibility into the cloud ecosystem. Cloud providers typically have a vast and complex infrastructure, which can make it challenging to monitor user activity and detect insider threats. Insider threats can occur when insiders, such as employees, contractors, or partners, intentionally or unintentionally access or disclose sensitive data.
Identity governance is the first step in securing data in the cloud. Across all of your on-premises and cloud platforms, workloads, and data access, you need a thorough, unified perspective. Identity management gives you the following:
Encryption is an essential security measure for protecting sensitive and important data, including Personally Identifiable Information (PII) and intellectual property, both in transit and at rest.
Third-party encryption solutions can offer additional layers of security and flexibility beyond what is provided by CSPs. For example, some third-party encryption solutions may offer more robust encryption algorithms or the ability to encrypt data before it is uploaded to the cloud. They can also provide granular access controls, enabling organizations to determine who can access specific data and under what circumstances.
Backing up cloud data is critical for data protection and business continuity. The 3-2-1 rule is a best practice, involving having at least three copies of the data, stored in two different types of media, with one backup copy stored offsite. Businesses should have a local backup in addition to the cloud provider’s backup, providing an extra layer of protection in case the cloud provider’s backup fails or is inaccessible.
IAM (Identity and Access Management) is essential for securing cloud resources and data. IAM components in a cloud environment include identity governance, privileged access control, and access management, such as SSO or MFA. To ensure effective IAM in a cloud environment, organizations must include cloud resources in their IAM framework, create appropriate policies and procedures, and regularly review and audit IAM policies and procedures.
Poor password hygiene is a common cause of security events. Password management software can help users create, store and manage strong, unique passwords for each account, making it easier to follow safe password procedures. This can encourage better password hygiene and reduce the risk of password-related security incidents.
MFA (Multi-factor authentication) is a security mechanism that adds an extra layer of security beyond traditional password-based authentication. It reduces the chance of credentials being stolen and makes it more challenging for threat actors to gain unauthorized access to cloud accounts.
MFA is particularly valuable in cloud environments, where many employees and contractors may access cloud accounts from various locations and devices. However, it is important to ensure that it is implemented correctly, easy to use, and integrated with existing security infrastructure and policies.
Your environment will get more complicated as you continue to utilize the cloud, particularly if you begin to rely on the hybrid multi-cloud. Data security in cloud computing is essential for reducing the dangers to your business and safeguarding not just your data but also your brand’s reputation.
Consider deploying solutions for controlling cloud access and entitlements to protect yourself from the always-changing cloud risks. For a thorough approach to identity management, incorporate these solutions into your entire IAM strategy as well.
A complete, identity-centered solution ensures that you constantly implement access control and employ governance more wisely, regardless of whether your data is on-premises or in the cloud. You will also profit from automation and other factors that increase identity efficiency and save expenses.
Cloud Computing Security: Foundations and Challenges
InfoSec Threats | InfoSec books | InfoSec tools | InfoSec services
Feb 28 2023
it is not uncommon for large organizations to face cyber attacks or data breaches, and it is important for them to have strong cybersecurity measures in place to prevent such incidents and mitigate their impact if they do occur. However, If such an incident did occur, the affected companies would likely conduct a thorough investigation and take appropriate steps to address the situation and prevent similar incidents from happening in the future.
The massive media and publishing business News Corp reported a data breach in February 2022, disclosing that its journalists had been the focus of an attack on a software supply chain. The breach revealed that the journalists had been hacked. The assets owned by News Corp. include a variety of prominent news sources, such as Dow Jones, FOX News, The Sun, and MarketWatch, amongst others. It is important to note that in March of 2019, the Dow Jones made news for disclosing a “screening list” that included critical information on terrorists, criminals, and shady enterprises. This information included names, addresses, and phone numbers.

The leak of thirteen million data took place on the FOX News website in April of 2022. The fifty-eight terabytes’ worth of information consisted of a variety of different things, including the company’s internal documents, the personally identifiable information (PII) of its workers, and many other things. Prior to the time when the firm was made aware of the occurrence, these documents continued to be accessible to the general public.
Today, the business has disclosed new information saying that the security breach really took place in February of 2020. This indicates that the hackers were present on the network for a period of two years before being discovered. Mandiant, which is now owned by Google, was the cybersecurity company that helped News Corp. back then. Because the perpetrators had access to the system for two years before they were discovered, it is highly likely that they were able to get away with stealing more information than was initially thought. Since no one knew it had been stolen, they would not have been on heightened alert for any potential attacks during that time.
The firm disclosed in a breach notice that the threat actors responsible for the incident gained access to its email and document storage system. This system is used by a variety of News Corp companies. The impacted workers’ personal and health information was obtained; nevertheless, the corporation has said that it does not seem that the activity was centered on exploiting personal information in any way.
The Wall Street Journal, the New York Post, and its news operations in the United Kingdom were among the News Corp publications that were compromised as a result of the security hack. Names, birth dates, social security numbers, driver’s license numbers, passport numbers, information about bank accounts, as well as information on medical and health insurance, were some of the pieces of personally identifiable information that were accessed.
News Corporation has indicated in the past that the assailants had links to China and were probably engaged in espionage operations to gather information for the benefit of China’s objectives.
The New York Post admitted that it had been hacked in October 2022, after discovering that its website and Twitter account had been exploited to distribute inappropriate information that targeted a number of different politicians in the United States. The newspaper eventually disclosed that one of its own workers was responsible for the incident, and that individual was terminated once their role in the scandal was uncovered.
Jan 03 2023
At the time of writing, a misconfigured server belonging to an Enterprise Resource Planning (ERP) Software provider based in California, United States was still exposing data to public without any security authentication or password.
An Elasticsearch server belonging to a major international IT recruitment and software solution provider is currently exposing the personal data of more than half a million Indian candidates looking for jobs.
However, the data is not limited to jobseeker as the server is also exposing the company’s employees’ data. Another important aspect of this data exposure is the fact that it also contains the company’s client records from different companies, including Apple and Samsung.
This was confirmed to Hackread.com by Anurag Sen, a prominent independent security researcher. What is worse, the server is still exposed and publicly accessible without any security authentication or password. Originally, the server was being exposed since late December 2022.
It all started when Anurag scanned for misconfigured databases on Shodan and noted a server exposing more than 6GB worth of data to public access. Anurag said that the server belongs to a company originally based in the United States with offices around the globe
including India. Whilst the database contains details of job seekers in India.
Hackread.com would not share the name of the company in this article because the server is still exposed.
Anurag’s analysis of the server revealed that the exposed records contain personal data of over 575,000 individuals, while the size of the data is over 6.3GB and increasing with new data with each day passing. This data includes the following:
The screenshot below shows the candidate details and client data that are currently being exposed:

The screenshot below was taken from the live server that shows the company’s client details. Some of these are top companies Apple, Samsung, Sandisk, Unilog, Moody, Intuit, NEC Corporation, Falabella and many more.
The company’s client list also indicates that its a high-profile business with a presence all over the globe.

Since the server is still live at the time of writing; Anurag alerted the Indian Computer Emergency Response Team over the weekend. However, there has been no response from the authorities yet.
India is home to almost 1.4 billion people. This makes the country a lucrative target for businesses as well as cybercriminals. The more the investment, the more widespread and vulnerable the IT infrastructure becomes.
Last year, several top data exposure-related incidents involving tens of millions of victims were reported from India. These included Indian Federal Police and banking records, Covid antigen test results, MyEasyDocs, online packaging marketplace Bizongo, etc.
It is yet unclear whether a third party accessed the database with malicious intent, such as ransomware gangs or threat actors. However, if it did, it would be devastating for the victim and the healthcare firm responsible for the server.
Furthermore, considering the extent and nature of the exposed data, the incident can have far-reaching implications, such as bad actors downloading the data, carrying out phishing scams, or identity theft-related fraud.
Hackers can hold the company’s server or data for ransom and leak it on cybercrime forums if their demands are not met. Nevertheless, the victims in this situation are the job hunters who trusted authorities with their personal information.
Misconfigured or unsecured databases, as we know it, have become a major privacy threat to companies and unsuspected users. In 2020, researchers identified over 10,000 unsecured databases that exposed more than ten billion (10,463,315,645) records to public access without any security authentication.
In 2021, the number increased to 399,200 exposed databases. The top 10 countries with top database leaks due to misconfiguration in 2021 included the following:

Data and Goliath: The Hidden Battles to Collect Your Data and Control Your World
Infosec books | InfoSec tools | InfoSec services
Jan 02 2023
Regula has presented their vision of the developments that will shape the industry’s landscape in 2023. Deepfakes, new cyber-hygiene norms, and demand for mature ID verification platforms are among some of the predictions for the next year.
While more and more industries move their customer experiences to digital, online identity verification is becoming an essential part of our life. It lets people cope with all sorts of mission-critical activities online: opening bank accounts, applying for benefits, getting insurance payouts, and even getting medical advice.
Still, the security of the digital IDV process is the number one concern that is forming the industry’s landscape and driving the majority of significant changes.
Javelin Strategy & Research reports that in 2022, identity fraud and scams cost $52 billion and affected over 42 million people in the US alone. The rising number of identity fraud cases, along with fraudsters’ hunger for personal information collected by service providers, will lead to three important changes in how data will be used and treated:
When it comes to more complex identity fraud cases related to synthetic media like deepfakes, experts expect to see a rise in amateur scam attempts along with the emergence of next-gen biometric-related fraud.
Both trends are developing in parallel and are powered by the same factor: the growing maturity and availability of machine-learning based technologies that make it possible to fake photos, videos, voices, and other characteristics previously considered unique.
Based on the opinion of Regula experts, all these trends will lead to a market that is developed enough to embrace mature end-to-end IDV solutions that are capable of not only verifying documents, but also biometric characteristics, like face, voice, and fingerprints.
“The good news is that minimal security measures are currently enough to repel 95% of possible attacks. The remaining 5% is where the difficulties lie. Now, most deepfakes are created for free, and they’re of such a quality that there’s no immediate danger. But that’s a matter of how many resources fraudsters will be willing to invest. At the moment, when they’re ready to spend significant amounts of money per deepfake, it’s a problem that requires interactive multi-layered protection. So if we picture the trends above as a scale, where convenience for the customer is on one end and security on the other, the balance is shifting to the latter,” notes Ihar Kliashchou, CTO at Regula.
In relation to this year’s trending topics — digital identity and decentralized identity — the company’s experts have their own take on that:

Infosec books | InfoSec tools | InfoSec services
Dec 08 2022
Before selling or trading in your laptop, it is important to prepare the device for its new owner as this will help ensure all of your personal data remains safe.
In an age when every day, a new version of a laptop with better features, sleek design, and improved performance hits the market, it is no wonder that you also wish to buy a new laptop to achieve excellence in performance and enjoy new features.
You have money, you can buy a new laptop, great! But what about your previous laptop? If you are thinking of selling it, then…stop.
If you think selling a laptop is all about saving your data, finding a seller, and selling it, then you need to think again. It goes beyond this! It is not all about getting a fair price, but also saving your personal information and private data from reaching a stranger – that might cost you a lot if that stranger is fraudulent or malicious.
Before selling or trading in your laptop, it is important to prepare the device for its new owner. This can be done by taking several simple precautions that will help ensure all of your personal data remains safe.
It goes without saying that your first step should be keeping a backup of your essential data, including personal and work-related files and folders, containing documents, presentations, emails, plans, strategies, or anything else that you have prepared with so much hard work.
If you don’t want to see your data slipping from your fingers, then this should be your number one step.
You can save your data on a data drive or upload it to a reliable cloud service. Or send them to your own email address (well, this is my favorite way of saving my data!). Do whatever suits you, but saving data is a must before selling your laptop.
However, this can only work if you have a few GB of data. In case you have terabytes of data then owning a workstation from companies like Western Digital (WD) is a good way to go.
Nobody wants the passwords of important accounts to get leaked. Full stop! But have you ever thought about how to save your passwords before giving your laptop? What — did you just say you can do it by signing off from all your accounts and deleting history and cookies? Ah, I wish it was really that easy, but it is not.
Where technology has brought so much ease into our lives, there it has also become a trouble in many ways — like this one. Unfortunately, some software can extract passwords even if you log out from your accounts.
That is where you should act smartly if you don’t want someone to sneak into your Facebook and start sending weird messages through your accounts to your friends. It could trigger so many controversies – eh. So, cut iron with iron.
You can also use apps such as password generators. One such example is the IPVanish password generator which lets users delete passwords permanently from their browsers. If you wish to do that manually, follow these easy steps:
For Chrome browser: First, open Chrome and click on the three-dot menu icon located in the top right corner. Then select “Settings” and click on “Passwords” under Autofill. Here you will find a list of all the websites that have saved credentials, along with their usernames and passwords.
Select an entry to see the details, then click on the three-dot menu icon next to it and select “Remove.” You’ll be asked to confirm by clicking “remove” again; once confirmed all login information for that website will be deleted from your computer. (Read more on Google.)
For Firefox: First, launch the Firefox browser on your device. Then, click the ‘Menu’ icon (three lines in the upper right corner) and select ‘Options’ or ‘Preferences’. In this menu, you will see a section for ‘Logins & Passwords. You can then scroll through all of your saved logins and passwords until you find the one that needs to be deleted.
For Safari Browser: To begin, open up the Safari browser on your computer and click the ‘Safari’ menu at the top left corner. In that menu option, select ‘Preferences’ and then navigate to the ‘Passwords’ tab. (Read more on Mozilla.)
Here you will see a list of all of your stored passwords that have been saved by Safari. To delete one or more of these passwords, simply check off each box next to each entry that you wish to remove and hit delete in the bottom right corner. (Read more on Apple.)
Have you saved your important data? Great! Now, what about data that is still on your laptop? Obviously, you can’t leave it like this for others to see your private information and confidential data. No, just deleting data files and clearing Recycle Bin or Shift + Delete might not work. It can still keep the issue of data leakage and privacy breaches there.
In this condition, most people go for drive formatting that cleans up your laptop and makes it data free. However, this method works if your files are overwritten and you are using a solid-state drive (SSD) with TRIM enabled.
With HDD or TRIM disabled, you would have to overwrite the hard drive if you don’t want cheap software to recover your data – yes, even after formatting. It is very easy to recover a permanently deleted file through even cheap software. So, be safe than sorry!
Once you are done saving your information, next, it is time to prepare your laptop for sale at a good price. The price of your gadget also depends on its model, functionalities, current market price, and a lot more. However, improving the outer condition, and speed, upgrading Windows, and enhancing the memory storage can enhance the price of your laptop.
So, work on the following things to get good bucks:

Dec 05 2022
The 50GB worth of data is currently being sold on two clear web forums with a price tag of 1 BTC per database.

A group of hackers has posted a trove of approximately 50GB of data for sale on two online forums and a Telegram group. The data was posted on 26 and 27th November 2022. This was revealed to Hackread.com by researchers at VPNMentor.
A probe into the incident revealed that the data belonged to 29 Israeli transportation, logistics services and forwarding firms. Researchers believe that the hackers breached a software provider’s single point of failure, gained unauthorized access to these logistics firms’ supply chains, and exfiltrated a trove of personal data and shipping records.
Hackers have posted the stolen data for sale. Visitors can buy a complete employee and customer information dataset from the targeted companies. The per-database rate is 1 BTC, which equals $17,000. An analysis of the graphics associated with these posts revealed that the data is part of a Black Friday Sale.
Previously, when some Israeli delivery firms were targeted in cyberattacks, the Israeli government’s cyber agencies named Iranian threat actors as the perpetrators. However, it is unclear if the same actors are responsible in this instance.
According to VPNMentor’s blog post, exposed data includes contract details and shipment information of the affected Israeli firms. The hackers have listed 1.1 million records for sale on different online forums. It seems like they have shared a small sample of data.
Whether 1 record represented 1 person or 1.1 million people were impacted in this data breach couldn’t be determined. The exposed information includes full names, addresses, and contact numbers.
Researchers were unsure whether the exposed addresses were work or home addresses. Customers’ exposed data includes full names and shipping details (sender and receiver’s addresses, number of packages, contact numbers, etc.).

These records can be exploited to intercept packages or blackmail/threaten courier firms’ employees into handing over valuable shipments. Threat actors can use personal data such as full names or contact details to target people with scams and phishing attacks.
Customers of these firms should be wary of suspicious SMS messages and calls and do not share personal information via phone. They should reveal sensitive data only to a trusted source only when necessary.
Sep 14 2022
There are many ways that data security risks can occur, and it is important to be aware of them in order to protect our information.
Data security issues, continuous data breaches, and advanced cyber-criminal activity make it harder for businesses to stay updated with the latest strategy to keep their accounts and customer data protected.
We continue to see companies small or large being targeted by cybercriminals, according to Nexor, the UK experienced a 31% rise in cyber-attacks during the height of the pandemic in May and June 2020.
Cybercrimes from malware, insider threats, and stolen data to hacked systems will always be a threat so how can companies ensure they are prepared for security risks as technology and cyber criminals continue to advance? We take a look at the top 3 data security risks business are facing.
Hackers and companies are aware of issues concerning IT infrastructures and computer systems, but it is the responsibility of the business to ensure systems are guarded and secure from unauthorised access and that they are not vulnerable to cybercriminal threats through unsecure internal networks and software.
A report in partnership with the office of cyber security and information assurance in the cabinet office, estimates the cost of cybercrime to the UK to be £27bn per annum.
As the pressure for cyber professionals rises, panic in business also increases as there is a shortage of IT security professionals with skills in IT and cyber security. The ISC 2021 Cybersecurity Workforce Study states that the global cybersecurity skills shortage has fallen for the second consecutive year, but the size of the workforce is still 65% below what it needs to be. CEO, Clar Rosso at ISC shares her thoughts:
“Any increase in the global supply of cybersecurity professionals is encouraging, but let’s be realistic about what we still need and the urgency of the task before us…The study tells us where talent is needed most and that traditional hiring practices are insufficient. We must put people before technology, invest in their development, and embrace remote work as an opportunity. And perhaps most importantly, organizations must adopt meaningful diversity, equity, and inclusion practices to meet employee expectations and close the gap.”
A UK government report published last year found that 48% of organisations lacked the expertise to complete routine cyber security practices, and 30% of organisations had skills gaps in more advanced areas, such as penetration testing, forensic analysis, and security architecture.
With a high demand for security professionals and a shortage in skills, could cyber criminals be a few steps ahead?
Many businesses, especially most small businesses lack the capability and expertise to withstand a cyber security attack. Finding the right talent and investing in the skills can be a challenge, but there are consultants that specialise in working with various types of businesses that can add value and help place the right data protection strategies and provide businesses with the best tools and training.
Guard Wisely are independent data security specialists that are trusted by organisations to solve their biggest compliance, security, operations, and BAU challenges. They have delivered many successful security projects to a large variety of Enterprise Customers Globally and over 180,000 employees.
The pandemic fast-forwarded the need for digitalisation, and the sudden change to remote working meant that more data was being shared across unsecure cloud environments, kept on networks and employee desktops. This meant an increased risk for businesses as they figured out how to maintain data security in a hybrid work environment.
We have seen that everything and everyone is connecting through the Internet, and wireless capabilities are bringing innovation to all areas of business and general life at unprecedented speed.
With remote and hybrid working being a part of the future of work, data needs to be regularly monitored and controlled. Large enterprises need to manage their customers’ and employees’ data to remain compliant, to do this they need to understand where that data resides to secure it.
Across the world, there are now nearly two billion internet users and over five billion mobile phone connections; every day, we send 294 billion emails and five billion SMS messages; every minute, we post 35 hours of video to YouTube, 3,000 photos to Flickr and nearly 35,000 ‘tweets’ according to this report .
Over 91 percent of UK businesses and 73 percent of UK households have internet access and £47.2 billion was spent online in the UK alone in 2009.
The issue arises for data security as the embedded operating system in any device is deployed in its firmware, and these operating systems are rarely designed with security as their prime focus. This means that many systems have flaws and vulnerabilities, which is a gateway for many hackers and cybercriminals.
With so many passwords to remember for a variety of devices, sites, and networks, we will continue to see a security risk in passwords. In most cases, hackers do not find it difficult to figure out corporate passwords and, employee passwords tend to be easier to work out.
Not only this, but once you know the password for a device, you’ll most likely be able to have access to other accounts. People tend to keep the same password across many of the accounts they hold, for the ease of remembering but this as much as we know it, is a security issue that needs to be addressed.
Unsecure passwords could increase ‘insider’ breaches at the workplace. Organisations often overlook the threats residing inside their ecosystems which can have devastating effects. These companies, although they are aware of threats don’t usually have an insider threat program in place, and are therefore not prepared to prevent, detect, and respond to internal threats.
Having access to anyone’s computers or devices at work can mean that systems will be at a higher risk of attack from insider threats. Hackers are always looking for opportunities to steal passwords and break them into private and corporate accounts.
To minimise these risks, companies must evaluate and introduce measures to ensure access to certain files and folders is in place. They will have to make sure individuals have unique passwords to enter their computers so that other people cannot access or abuse computer activity.
Tracking which files and folders are being used and accessed on individual machines will also be beneficial in a lot of cases. As a short-term fix, they can also ensure they turn on two-factor authentication (2FA), also known as multi-factor authentication where possible for important accounts, as a secondary method of authentication.

Business Data Networks and Security
Sep 01 2022

August 2022 has been a lesson in being careful with whom you provide sensitive information. In a month that saw the former US president accused of misappropriating classified government documents, there were also a spate of malicious insiders compromising their employer’s systems.
Meanwhile, the bastion of password security, LastPass, announced that its systems had been breached – although the organisation is confident that customers’ details remain secure.
In total, we identified 112 publicly disclosed security incidents in August, resulting in 97,456,345 compromised records.
You can find the full list of incidents below, broken into their respective categories.
Contents
Data Breaches

Data Security

Free Basic network and Data Security Awareness

Aug 25 2022
The popular researcher Mordechai Guri from the Ben-Gurion University of the Negev in Israel devise an attack technique, named GAIROSCOPE, to exfiltrate data from air-gapped systems using ultrasonic tones and smartphone gyroscopes.
The attack requires that the threat actor has in advance installed malware on the air-gapped system, as well as on a smartphone which must be located in the proximity of the system.
The malware installed in the air-gapped system generates ultrasonic tones in the resonance frequencies of the MEMS gyroscope which produce tiny mechanical oscillations within the smartphone’s gyroscope.
The frequencies are inaudible and the mechanical oscillations can be demodulated into binary information.

The researcher pointed out that the gyroscope in smartphones is considered to be a ’safe’ sensor and can be used legitimately from mobile apps and javascript without specific permissions, unlike other components like the microphone.
The researchers added that in Android and iOS, there may be no visual indication, notification icons, or warning messages to the user that an application is using the gyroscope, like the indications in other sensitive sensors.
“Our experiments show that attackers can exfiltrate sensitive information from air-gapped computers to smartphones located a few meters away via Speakers-toGyroscope covert channel.” reads the research paper.
The malware on the air-gapped system gather sensitive data, including passwords and encryption keys, and encodes it using frequency-shift keying. In frequency-shift keying (FSK), the data are represented by a change in the frequency of a carrier wave.
Then the malware uses the device’s speakers to transmit the sounds at the inaudible frequencies.
On the receiving side, the phone receives the sounds using the device’s gyroscope and the malware running on the phone continuously samples and processes the output of the gyroscope. When the malware detects an exfiltration attempt, which is started using a specific bit sequence, it demodulates and decodes the data. The exfiltrated data can then be sent to the attacker using the phone’s internet connection.
“In the exfiltration phase, the malware encodes the data and broadcast it to the environment, using covert acoustic sound waves in the resonance frequency generated from the computer’s loudspeakers. A nearby infected smartphone ‘listens’ through the gyroscope, detects the transmission, demodulates and decodes the data, and transfers it to the attacker via the Internet (e.g., over Wi-Fi).” continues the paper. “The air-gapped workstation broadcasts data modulated on top of ultrasonic waves in the resonance frequencies that oscillates the nearby MEMS gyroscope. The application in the smartphone samples the gyroscope, demodulates the signal, and transmits the decoded data to the attacker through Wi-Fi.”
The test conducted by the researcher demonstrated that the GAIROSCOPE attack allows for a maximum data transmission rate of 8 bits/sec over a distance of up to 8 meters.
The following table shows the comparison with the existing acoustic covert channels previously devised by the researchers:

The researcher also provide countermeasures to mitigate the GAIROSCOPE attack, such as speakers elimination and blocking, ultrasonic filtering, signal jamming, signal monitoring, implementing sensors security, keping systems in restricted zones defined by a different radius, depending on the zone classification.
Jul 26 2022
Just under a year ago, the US arm of telecomms giant T-Mobile admitted to a data breach after personal information about its customers was offered for sale on an underground forum.
At the time, VICE Magazine claimed to have communicated with the hacker behind the breach via online chat, and to have been offered “T-Mobile USA. Full customer info.”
VICE’s Motherboard reporters wrote at the time that:
The data include[d] social security numbers, phone numbers, names, physical addresses, unique IMEI numbers, and driver licenses information, the seller said. Motherboard has seen samples of the data, and confirmed they contained accurate information on T-Mobile customers.
IMEI is short for International Mobile Equipment Identity, a globally unique serial number burned into your phone when it’s manufactured. Because the IMEI is considered a “non-resettable identifier”, apps on both Android and iOS are restricted from accessing it unless they have been granted special device management privileges, and developers are instructed to rely on user-resettable identifiers such as advertising IDs when legitimately tracking users and devices. You can view your phone’s IMEI by dialling the special phone number *#06#.
Reuters reports that T-Mobile has agreed, in a US federal court in Missouri, to make $350,000,000 available for what are known in America as class-action settlements.
Class actions involve individuals, who would otherwise need to sue individually for impossibly small amounts, banding together with a team of attorneys to bring lawsuits that combine their individual complaints.
Part of the $350 million mega-settlement, says Reuters, is up to $105,000,000 (30% of the total amount) for the lawyers, leaving a slightly less dramatic $245 million for the individuals who joined the suit.
Apparently, more than 75 million people were affected in the breach, though with the standard payout listed by Reuters as $25 per person, it looks as though fewer than 10 million of them decided to sign up to be part of the legal action.
According to Reuters, T-Mobile will also commit to spending “an additional US$150 million to upgrade data security”, bringing its total settlement pledge to half-a-billion dollars.
In return, T-Mobile doesn’t have to admit guilt, so this isn’t a fine or a criminal penalty – it’s a civil agreement to settle the matter.
The settlement still needs approval from from the court, something that’s expected to happen by the end of 2022.

#InfoSecTools and #InfoSectraining
Ask DISC an InfoSec & compliance related question
Jun 01 2022
Researchers from Shadow Server scanned the internet for publicly accessible MySQL server instances on port 3306/TCP and uncovered 3.6M installs worldwide responding to their queries.
These publicly accessible MySQL server instances represent a potential attack surface for their owners.
“These are instances that respond to our MySQL connection request with a Server Greeting. Surprisingly to us, we found around 2.3M IPv4 addresses responding with such a greeting to our queries. Even more surprisingly, we found over 1.3M IPv6 devices responding as well (though mostly associated with a single Autonomous System).” states the report published by the researchers.
Most of the accessible IPv4 MySQL servers are in the United States (740.1K), China (296.3K), Poland (207.8K) and Germany (174.9K).

Accessible IPv4 MySQL servers
Most of the accessible IPv6 MySQL servers are in the United States (460.8K), Netherlands (296.3K), Singapore (218.2K) and Germany (173.7K).
Researchers recommend admins follow the MySQL 5.7 Secure Deployment Guide and MySQL 8.0 Secure Deployment Guide for the deployment of their servers.
“It is unlikely that you need to have your MySQL server allowing for external connections from the Internet (and thus a possible external attack surface). If you do receive a report on your network/constituency take action to filter out traffic to your MySQL instance and make sure to implement authentication on the server.” concludes the report.
The researchers shared data on the accessible MySQL instances in the Accessible MySQL Server Report.
Over 3.6 million MySQL servers found exposed on the Internet
PHP & MySQL: Server-side Web Development
Mar 22 2022
The gang announced the alleged hack through its Telegram channel and shared a series of screenshots as proof of the hack. Some of the images published by the threat actors appear to be related to the company’s customer data.
The message published by the group claims that the gang had Superuser and Admin access to multiple systems of the company.

The company is investigating claims of a data breach which, if confirmed, could pose serious risks to the customers of the company.
“Okta is aware of the reports and is currently investigating,” states a spokesperson for the company. “We will provide updates as more information becomes available.”
Todd McKinnon, CEO at Okta, confirmed that in late January 2022, the company detected an attempt to compromise the account of a third party customer support engineer working for one of its subprocessors.
McKinnon added that there is no evidence of ongoing malicious activity that resulted from the activity detected in January.